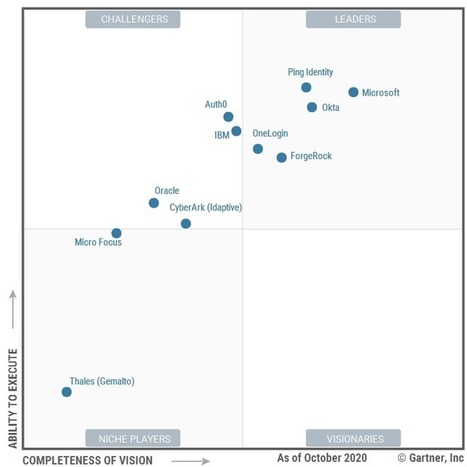
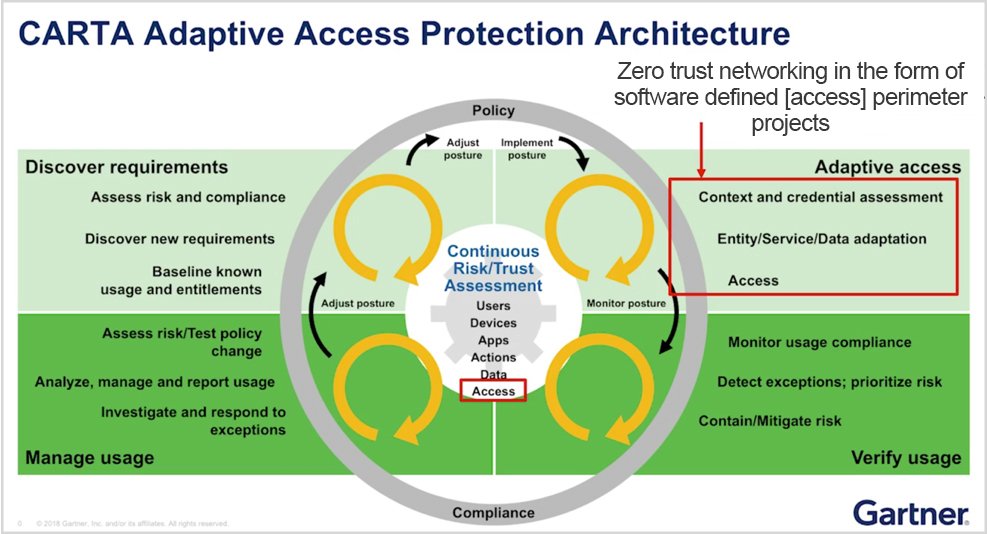
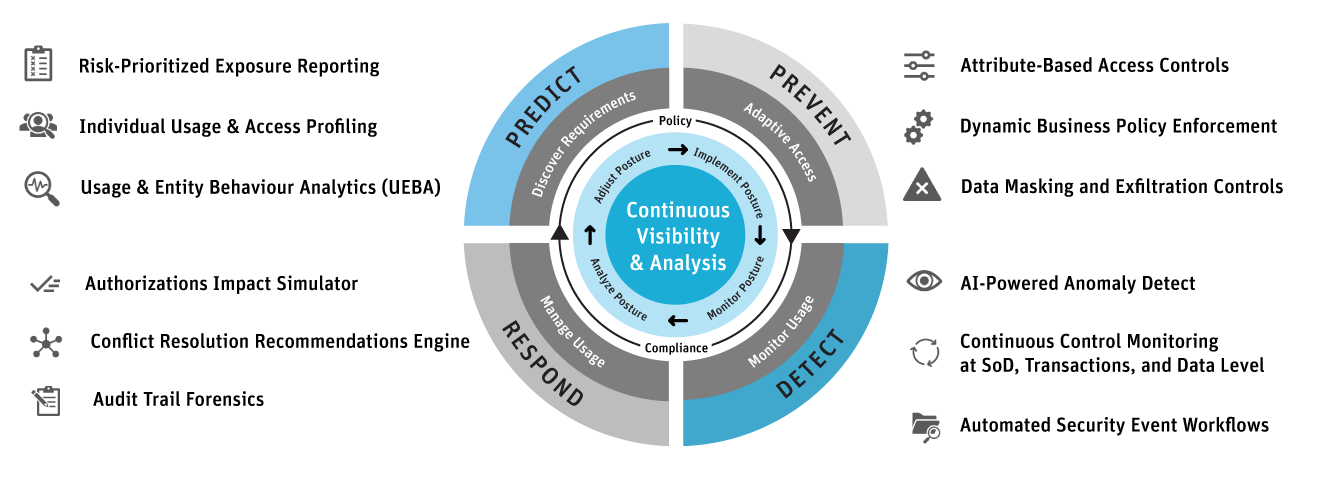
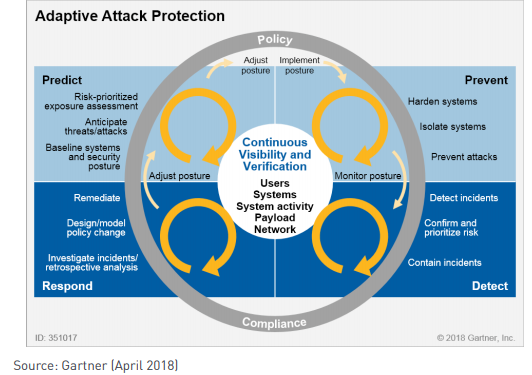
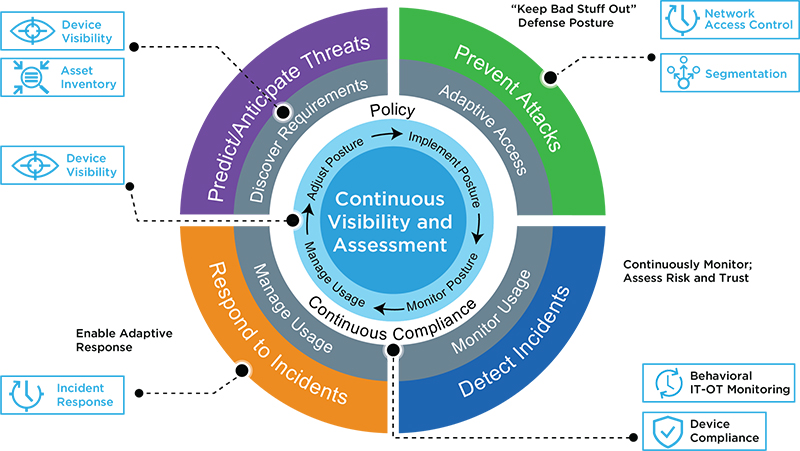
טוויטר \ Interset AI בטוויטר: "#GartnerSEC: Our world view is flawed. We need #CARTA (Continuous Adaptive Risk and Trust Assessment) that allows us to predict, prevent, detect and respond to security threats,

Gartner for IT op Twitter: "CARTA shifts thinking about access control as a static behavior to thinking that it needs to be continuously assessed. #GartnerCAT https://t.co/fgkpOvNBRa" / Twitter
Feasibility Study between Continuous Adaptive Risk and Trust Assessment and Organic Networks, Computer Science - Commercial Info